Getting started
Getting started
This QuickStart will walk you through Oplane’s core features
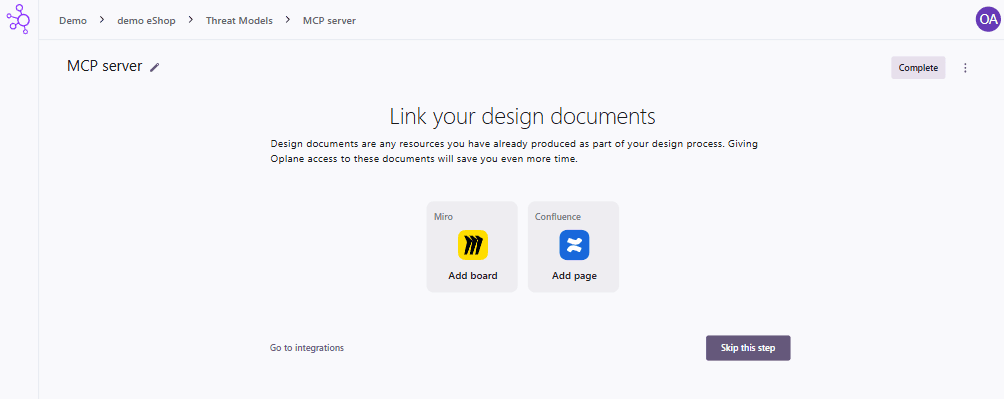
This guide assumes that you are using automated onboarding, for example through the Oplane Slack integration. When a new threat model has been assigned, you will see a page like this:
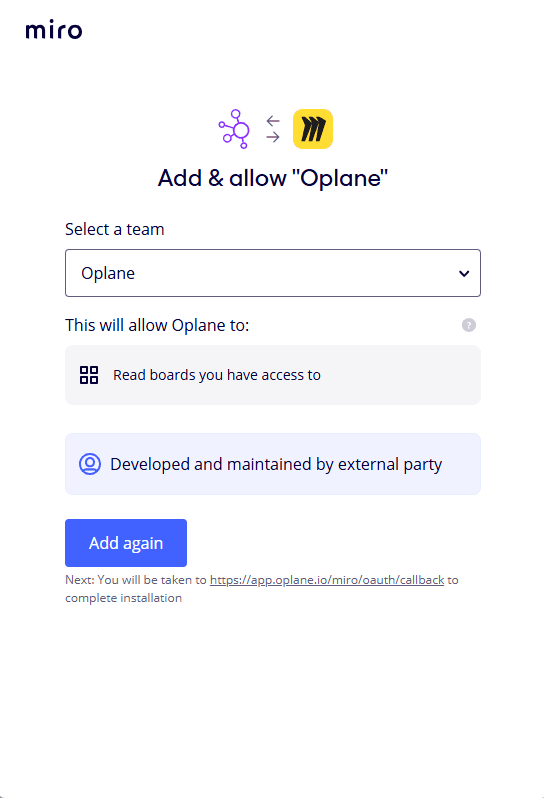
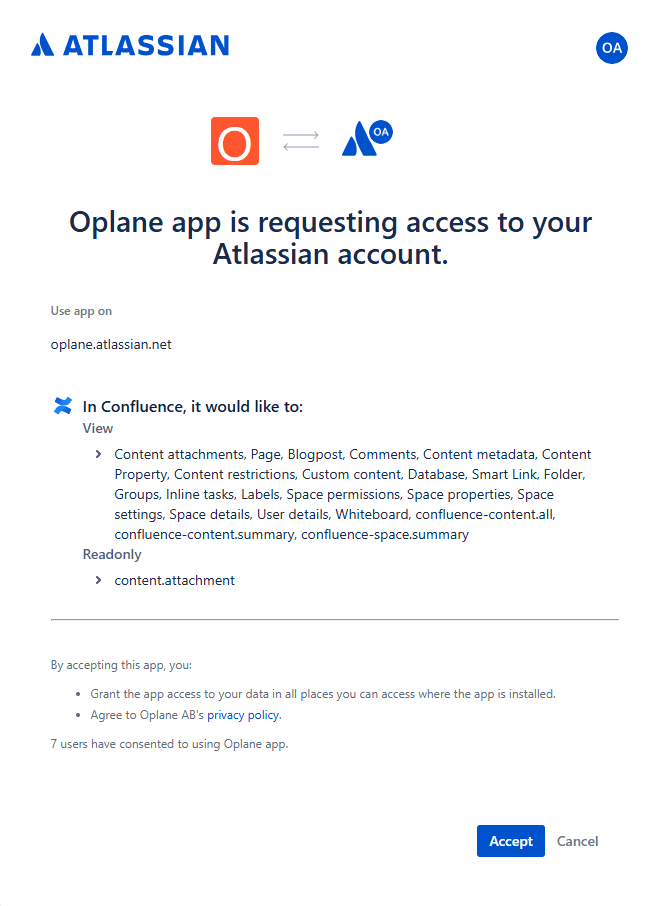
You can then add a Miro or Confluence integration via OAuth.
We will use a Miro board in this example.
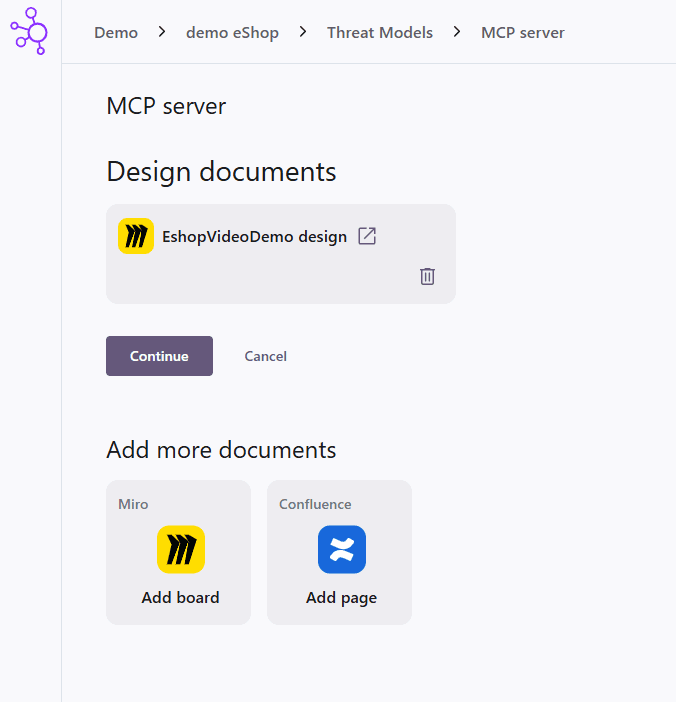
Add the board URL and then press Continue. The design documents will then be imported.
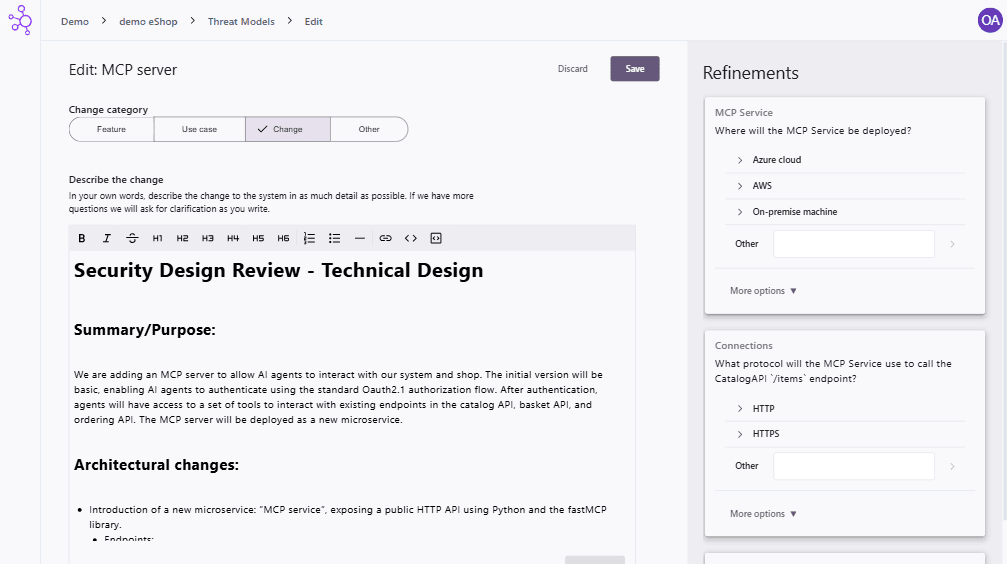
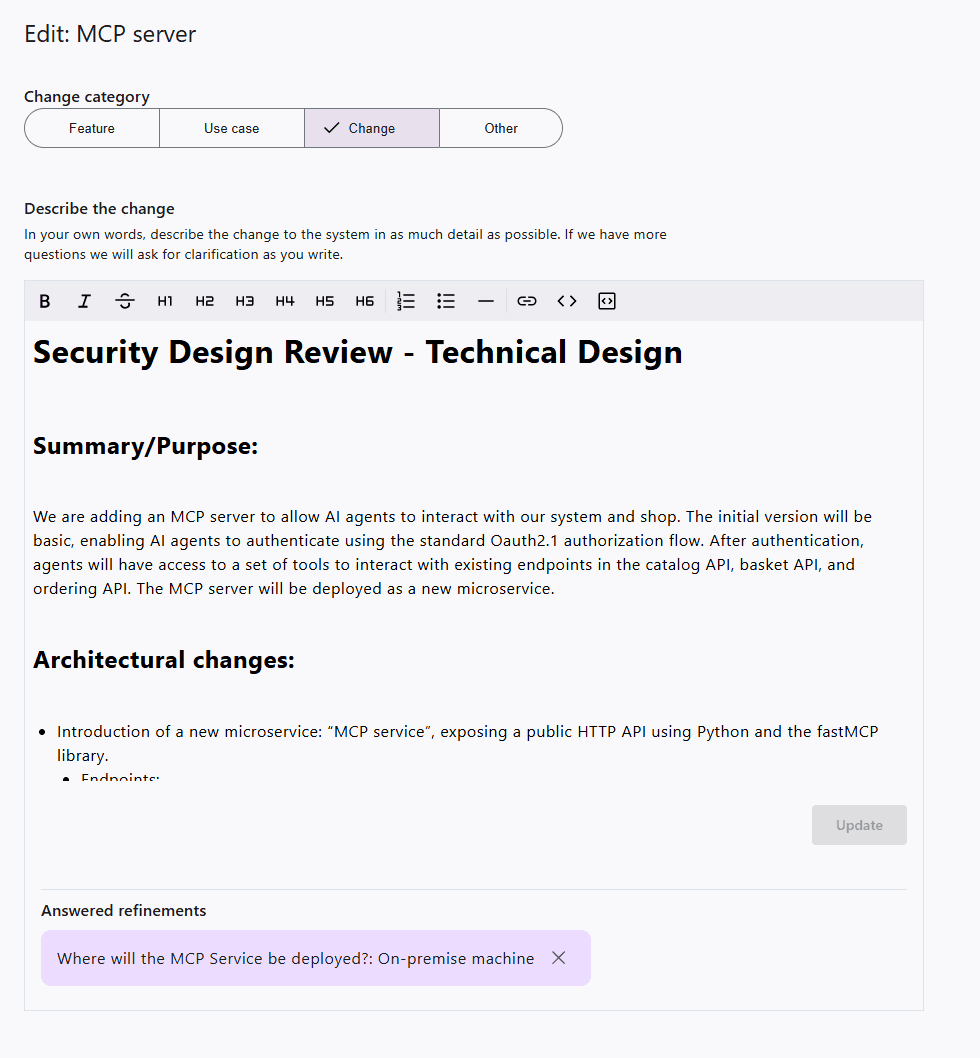
You can, of course, skip importing any design documents, but you will then have to manually describe the change you want to make. After the import has finished, you will see a change description and refinement questions.
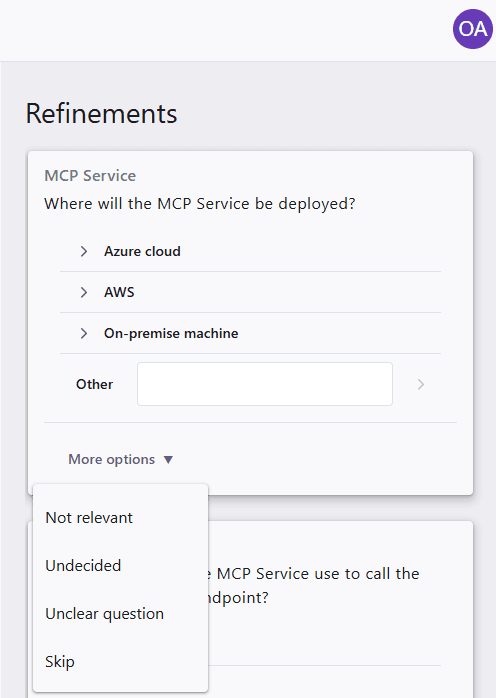
Start by verifying that the change text reflects the actual change you intend to make. If an update is necessary, you can modify the text and then click Update. When you are satisfied with the change text, you can start answering the refinement questions. If you cannot or do not want to answer a question, you can select More options for each question. There, you can choose from Not relevant, Undecided, Unclear question, or Skip. When you select one of these options, the question will be removed from the refinements list.
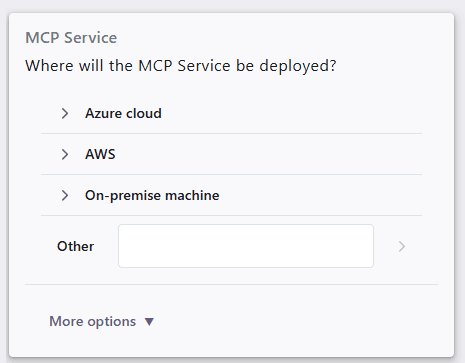
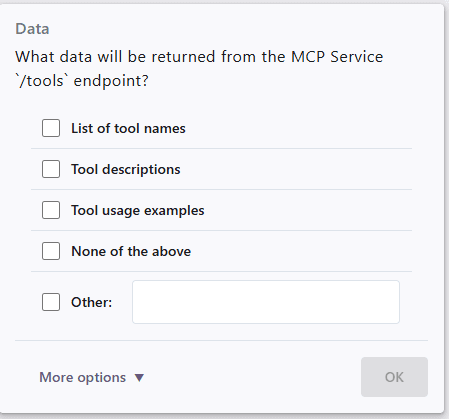
Refinements can be either single-choice or multiple-choice. If you are not satisfied with the pre-filled answers, you can always select Other and provide a free-text response.
If you accidentally select the wrong answer, you can delete it under Answered refinements. The refinement question will then reappear in the list.
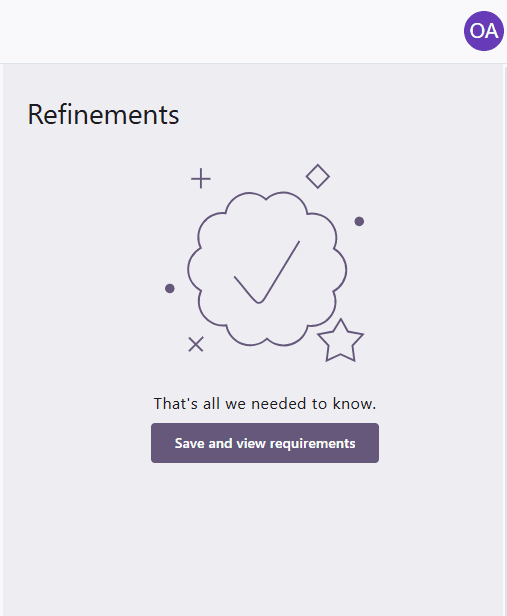
When you have finished answering the refinement questions, you will see a screen that says "That's all we needed to know." Press Save and view requirements to continue.
Oplane will now generate requirements based on your answers.
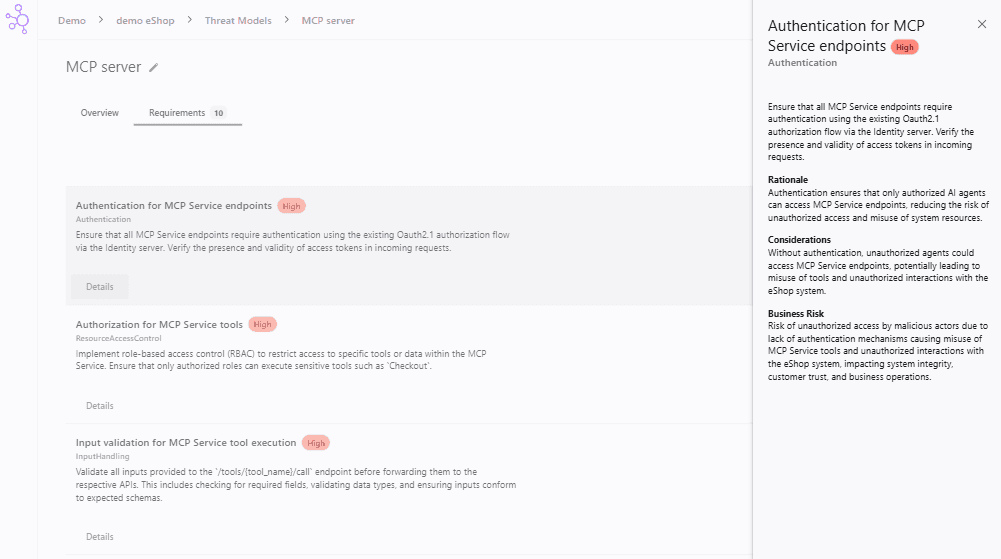
When the requirements have been generated, they will appear in a list. We will now go through the automatically created requirements to ensure that the system changes will be implemented securely.
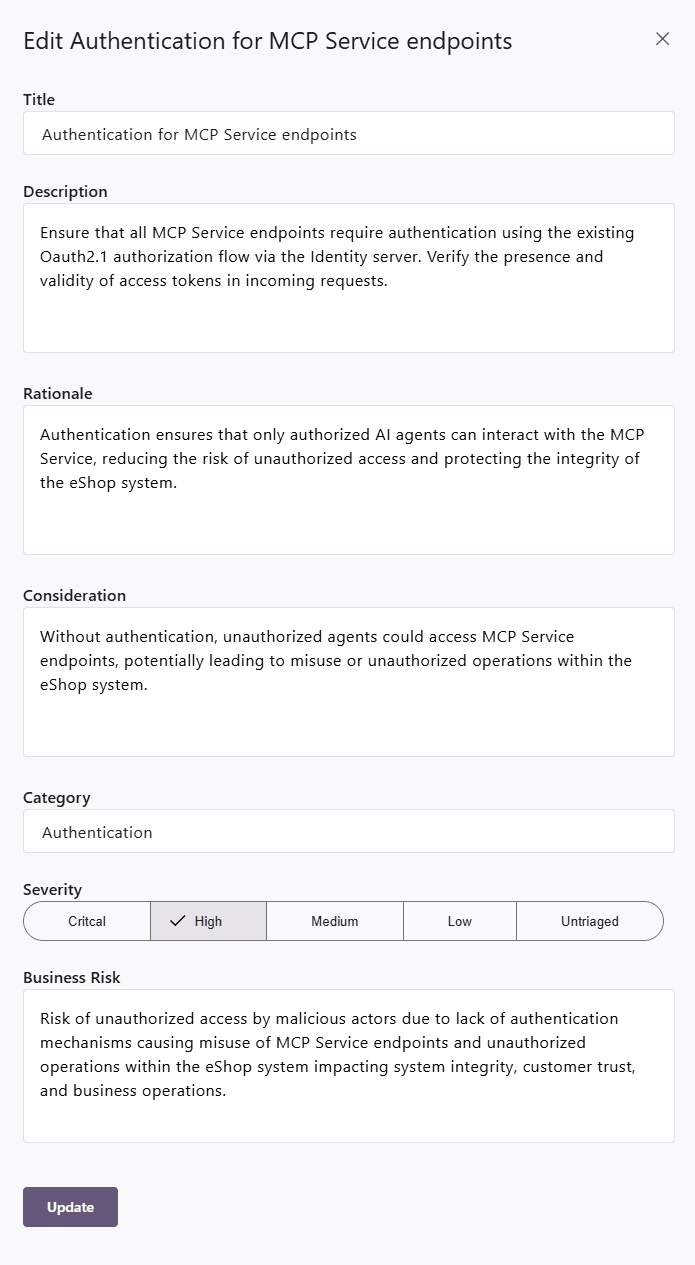
For every requirement, you can press Details to see why the requirement was added and what business risk it addresses.
If you want to make a change, you can press the three dots (ellipsis) next to the requirement and select Edit.
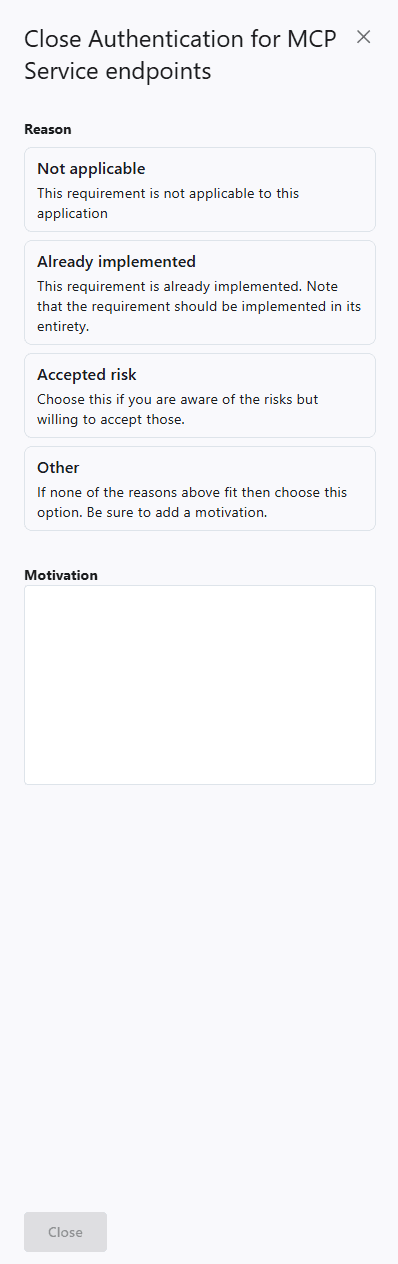
If the requirement is not valid, you can choose to close it instead.
You can also comment on each requirement by pressing the chat bubble.
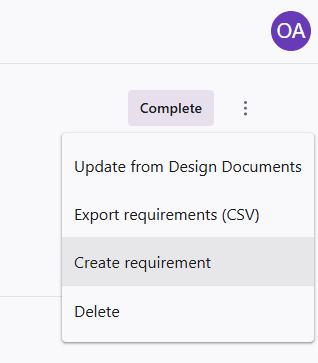
If you want to create a custom requirement, you can do that as well. Press the three dots (ellipsis) next to Complete, and from there you can create a new requirement.
When every requirement has been evaluated, you can click Complete. This will mark the threat model as completed and run any organizationally defined tasks, such as creating issues.